5 Simple Techniques For Risk Management Enterprise
The Best Guide To Risk Management Enterprise
Table of ContentsThe Best Strategy To Use For Risk Management EnterpriseThe 30-Second Trick For Risk Management EnterpriseThe Ultimate Guide To Risk Management Enterprise6 Simple Techniques For Risk Management EnterpriseRisk Management Enterprise Can Be Fun For EveryoneAll about Risk Management EnterpriseThe Best Guide To Risk Management Enterprise
Real-Time Risk Assessments and Reduction in this software program permit organizations to constantly monitor and review threats as they advance. Once risks are recognized, the software program promotes prompt reduction actions.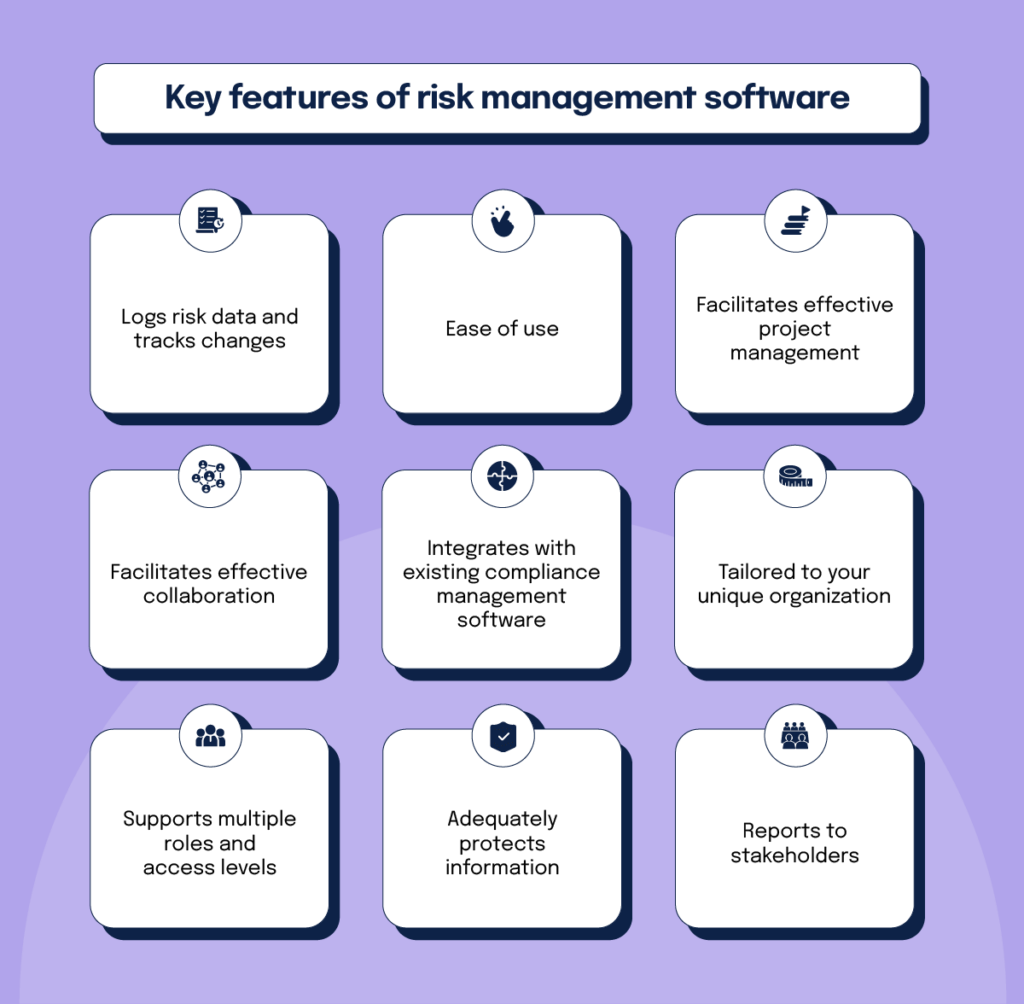
KRIs fix the trouble of inconsistent or unclear threat analysis. They address the obstacle of ongoing threat administration by offering tools to check dangers continually. KRIs improve protection threat oversight, making sure that possible risks are recognized and taken care of successfully. The task of threat monitoring need to not be an obstacle. Companies need to depend on a superior and sophisticated risk monitoring software.
A Biased View of Risk Management Enterprise
IT risk administration is a subset of business threat monitoring (ERM), created to bring IT run the risk of in accordance with a company's danger cravings. IT run the risk of management (ITRM) includes the policies, treatments and technology needed to lower risks and vulnerabilities, while keeping compliance with applicable governing requirements. Furthermore, ITRM seeks to limit the effects of harmful occasions, such as protection violations.
Veronica Rose, ISACA board supervisor and an info systems auditor at Metropol Corp. The ISACA Threat IT framework aligns well with the COBIT 2019 framework, Rose claimed.
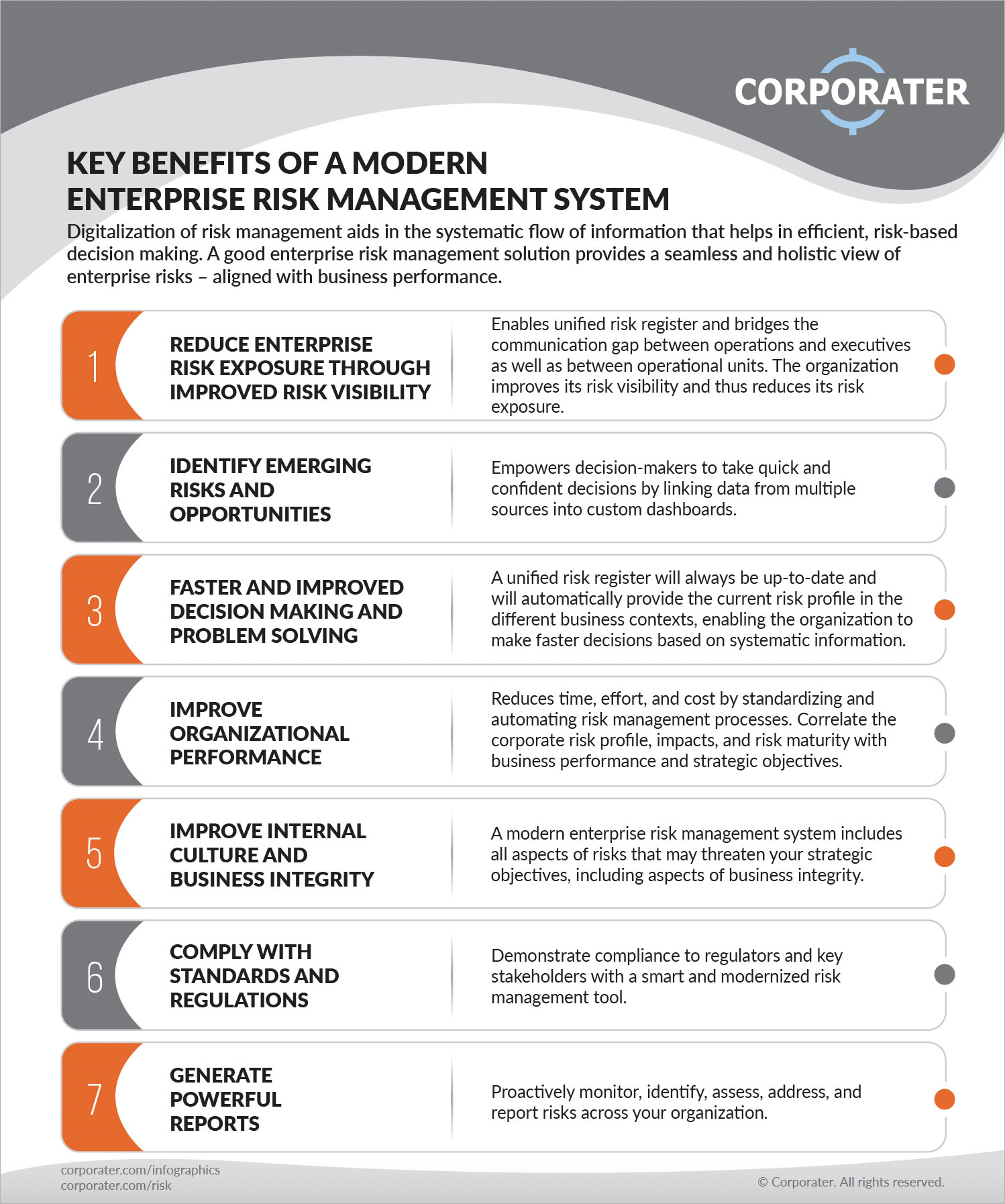
Venture Threat Administration Software Application Growth: Advantages & Characteristics, Expense. With technical developments, dangers are continuously on the rise., companies browse with a constantly changing sea of threats.
Some Known Details About Risk Management Enterprise
In this blog site, we will certainly dive into the globe of ERM software application, exploring what it is, its advantages, functions, and so on so that you can develop one for your company. Venture Danger Management (ERM) software is the application program for planning, directing, arranging, and controlling organization tasks and enhancing risk monitoring procedures.
With ERM, organizations can make informative decisions to improve the general durability of business. Read: ERP Application Advancement Dedicated ERM systems are crucial for companies that frequently manage vast quantities of sensitive details and multiple stakeholders to authorize calculated choices. Some markets where ERM has actually ended up being a typical system are health care, money, construction, insurance policy, and infotech (IT).
: It is demanding for any kind of venture to undertake a comprehensive audit. Nonetheless, it can be prevented by using the ERM software system. This system automates regulation compliance monitoring to maintain the organization safe and compliant. Besides that, it likewise logs and categorizes all the files in the system making it less complicated for auditors to assess processes a lot quicker.
The Ultimate Guide To Risk Management Enterprise
You can likewise attach existing software program systems to the ERM through APIs or by including data by hand. Businesses can utilize ERM to assess risks based on their possible influence for far better risk monitoring and mitigation.: Adding this function enables users to get real-time notices on their tools about any type of threat that might happen and its effect.
Instead, the software application permits them to set thresholds for various processes and send out push alerts in situation of possible threats.: By integrating information visualization and reporting in the personalized ERM software program, companies can gain clear insights concerning threat fads and performance.: It is obligatory for organizations to stick to market conformity and regulative requirements.
These platforms allow firms to implement best-practice threat administration procedures that straighten with industry standards, using an effective, technology-driven strategy to determining, analyzing, and mitigating dangers. This blog explores the benefits of automatic danger monitoring devices, the locations of risk management they can automate, and the value they offer a company.
5 Simple Techniques For Risk Management Enterprise
Groups can establish types with the pertinent fields and quickly produce various forms for various risk kinds. These risk evaluation kinds can be flowed for completion using automated workflows that send notifications to the relevant team to complete the kinds online. If forms are not finished by the deadline, after that chaser emails are immediately sent out by the system.
The control surveillance and control screening procedure can likewise be automated. Companies can make use of computerized operations to send out routine control test notices and staff can enter the results through online types. Controls can likewise be checked by the software by establishing rules to send out notifies based on control information kept in click resources various other systems and spread sheets that is drawn right into the platform via API combinations.
Threat management automation software program can likewise support with threat coverage for all levels of the business. Leaders can see reports on risk direct exposure and control effectiveness with a selection of reporting outcomes including static records, Power BI interactive reports, bowtie analysis, and Monte Carlo simulations. The ability to pull actual time reports at the touch of a button removes difficult information control jobs leaving threat teams with even more time to evaluate the information and recommend business on the best strategy.
Organizations operating in affordable, fast-changing markets can not pay for hold-ups or inadequacies in dealing with possible dangers. Traditional risk management using hands-on spreadsheet-based processes, while acquainted, frequently lead to fragmented data, lengthy reporting, and a boosted probability of human mistake.
Not known Facts About Risk Management Enterprise
This makes sure threat signs up are always current and aligned with organizational purposes. Conformity is one more essential driver for automating risk monitoring. Criteria like ISO 31000, CPS 230 and COSO all offer guidance published here around threat monitoring ideal methods and control frameworks, and automated risk monitoring tools are structured to line up with these demands aiding firms to fulfill most frequently used risk monitoring standards.
Look for danger software application platforms with a permissions pecking order to easily establish operations for threat rise. This functionality enables you to tailor the sight for each customer, so they just see the data pertinent to them. See to it the ERM software application offers user monitoring so you can see who entered what information and when.
Go with a cloud-based system to ensure the system obtains normal updates from the vendor adding brand-new capability. Choose tools that provide task threat administration capacities to handle your projects and profiles and the connected threats. The benefits of taking on risk management automation software extend far beyond performance. Companies that integrate these services right into their ERM technique can expect a host of concrete and abstract.

Not known Details About Risk Management Enterprise
While the case for automation is compelling, carrying out a risk management system is not without its difficulties. To conquer the obstacles of danger monitoring automation, companies must spend in data cleaning and governance to make certain a strong structure for carrying out an automated platform.
Automation in danger administration empowers businesses to find more transform their approach to risk and build a stronger structure for the future (Risk Management Enterprise). The question is no much longer whether to automate threat monitoring, it's just how quickly you can begin. To see the Riskonnect in action,
The answer frequently hinges on how well threats are prepared for and taken care of. Job management software program works as the navigator in the troubled waters of task implementation, offering tools that recognize and assess dangers and design strategies to reduce them successfully. From real-time information analytics to detailed danger tracking dashboards, these tools give a 360-degree view of the task landscape, enabling task supervisors to make informed choices that keep their tasks on track and within budget.